…And how does multi-factor authentication protect your business from hackers?
When you’re learning about the world of malware, hacking and cyber-security, you’ll hear a number of terms being thrown around that you might not understand. One of those is multi-factor authentication, also known as two-factor authentication or 2FA.
This is a second level of security for your online accounts that is quickly becoming essential in terms of safeguarding your accounts and keeping the cyber-criminals at bay.
What does multi-factor or two-factor authentication mean?
When you’re applying for a new bank account or most any government program, you’re likely to be asked for two pieces of ID, to prove that you are who you say you are. The theory is that if you are trying to commit fraud or steal someone else’s identity, you may have forged or stolen their driver’s license, but it’s much less likely that you also were able to forge a credit card with the same name on it. That second piece of “authentication” or proof of your identity, makes it infinitely more likely that you are legit.
Likewise, think of a password as your online identification. If someone guesses your email password, and your email provider only has single-factor authentication, they can log into your email, and pretend to be you. Scary thought, right? (Read our piece on what makes a good password to protect yourself.)
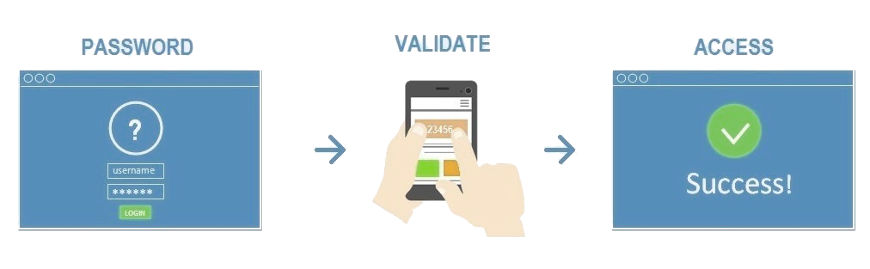
With multi-factor authentication, after you enter your ID and password, the system might send you a text to your mobile phone with a code. To finalize your email login, you would be prompted to enter the code that you received. So then, to steal your identity and use your email, a hacker would not only have to guess your password, they would have to also steal your phone or intercept the text. How likely is that? Sure, it could happen, but again, it’s much less likely than simply guessing your password, so this method is much more secure than single-factor authentication.
Is two-factor authentication the same as two-step authentication?
There is some difference of opinion out there about the difference between two-factor authentication and two-step authentication. The strictest definition of two-factor authentication requires you to use at least two of the following:
- Something you know (typically a password)
- Something you are (thumb-print, face recognition, retinal scan etc.)
- Something you have (like a smartphone or token)
Some security experts think that a verification code that is sent to your phone is actually not two-factor authentication, because the code is just another example of something you know. Others say that because the code is sent to your phone, it counts as something you have. We won’t weigh in, but suffice to say that regardless of the definition, the second step dramatically improves security.
Which business systems require multi-factor authentication?
The best answer to this question is all of them. In your business, you may have general logins for your employees to access the network, their laptops, or both. You may have a different login for email, and then logins for things like accounting systems, CRMs etc. Each of these systems contains critical business data and unauthorized access could be hugely damaging. Use multi-factor authentication wherever you can. Users will feel inconvenienced at first, but after a while, it just becomes part of the process.
What can you use as secondary authentication as part of 2FA?
Multi-factor authentication usually uses a password as the first method of authentication. Once you enter the correct password, a number of different methods can be used as that critical second step. These include the following:
SMS or text message:
As noted in the example above, by requiring you to enter a code that was sent to your cellphone, the system is able to use something that is unique to you (your cell number) to add that second level of security. Obviously, if you use text as your second method of authentication, you would need to ask for a valid cell number whenever a user creates a new account in your system. This is the most common method used for 2FA. Many security experts have warned that SMS is not a secure form of communication, and can be intercepted, but if it’s your only option, it’s still much better than single-factor authentication.
Email:
This would work just like the text method above. The system sends a code, in this case via email, and the user is prompted for that code after entering his/her password. Obviously, this wouldn’t be practical if the account you’re trying to protect is an email account.
Phone call:
If your employees prefer voice over text, you can set up your system to auto-generate a voice call that would read out a 5-10 digit verification code.
Tokens:
This is a little more high-tech, but very secure. A token is a small device that you give to the user. That device constantly cycles through different verification codes. One code may be valid for no more than a minute. When the user enters their password, they will be prompted for a code, which will be different every time because the token is constantly changing it. Authenticator apps like Google Authenticator, Authy or Microsoft Authenticator can essentially turn your phone into a token for this purpose.
Biometrics:
This is another fancy word that gets thrown around a lot, but biometrics simply means that a system uses unique physical information about you to verify your identity. This can be face recognition, a thumb print, or even a retinal scan. The technology for this kind of authentication is more advanced, but biometrics can be a very secure method of authentication. If a system is using biometrics, after you enter your password, you would be prompted to place your thumb on a sensor etc.
How do I add 2FA to my business apps?
The good news is that most business and personal apps are now built with multi-factor authentication as an option. Others allow you to use third-party authentication apps to add that extra layer of security. If your business uses custom-built in-house apps, there are fairly simple ways to add two-factor authentication, and it’s in your best interest to do so.
What else can your business do to protect against hackers and malware?
We have a number of excellent resources related to cyber security that can help you familiarize yourself with the threats that are out there in the cyber universe, and understand what strategies you can employ to stay ahead of cyber-criminals. Of course, there is no way to make cyber-security 100% effective, so it’s a good idea to talk to one of our cyber insurance brokers about how a cyber policy can protect your business when all else fails and your systems are compromised.
Looking for business insurance?
Speak with a Mitch Insurance broker today to get a quote on Ontario business insurance. Learn more >
Call now
1-800-731-2228







